Right this way to 2FA
Audience
This is the second in a series of posts focusing on helping others adopt security tools or practices. The goal here is to approach these as you would a checklist. We’ll explore the following:
Password manager post here 👈 👀
Two-factor authentication ✅ 👈 you are here
Browser security 🔜
HaveIbeenPwned 🔜
Speed dating Intro to Threat Modeling 🔜
If you’re a seasoned security engineer or “tech savvy” the information will likely be familiar to you. However the descriptions or perspective in this blog post may be useful in explaining concepts or empowering others. Come along for the ride.
What is two-factor authentication?
Two-factor authentication is a specific form of multifactor authentication that strengthens access security by requiring something you know and something you have to verify your identity. This “second factor” is usually one of the following:
Something you know (knowledge element): a password, pin, or answers to security questions
Something you have (possession element): a time based six digit code from an application like Google Authenticator or Authy, or, a hardware key such as a Yubikey.
Something you are (inherence): biometric auth like a fingerprint scan or FaceID on iOS.
Why do you need it?
As we read previously, bad password hygiene is still quite commonplace. Coupled with the prevalence of data breaches it's imperative that a username and password pair is not the only mechanism to verify your identity. A bad actor must possess your second factor to access your account. Two factor authentication can also help protect against credential stuffing and phishing attacks.
What are the different kinds of 2FA?
SMS
SMS 2FA is the now ubiquitous method of validating user identity by texting a security code to a mobile device.
Image source: Google
TOTP
The Time-Based One Time Password (TOTP) method generates a private key on your device. The security key is presented to you in the form of a QR code that is scanned into an application such as Google Authenticator or Authy. The passcodes generated by the authenticator expire after a certain period of time (generally sixty seconds) after which a new code is generated.
Image source: Google
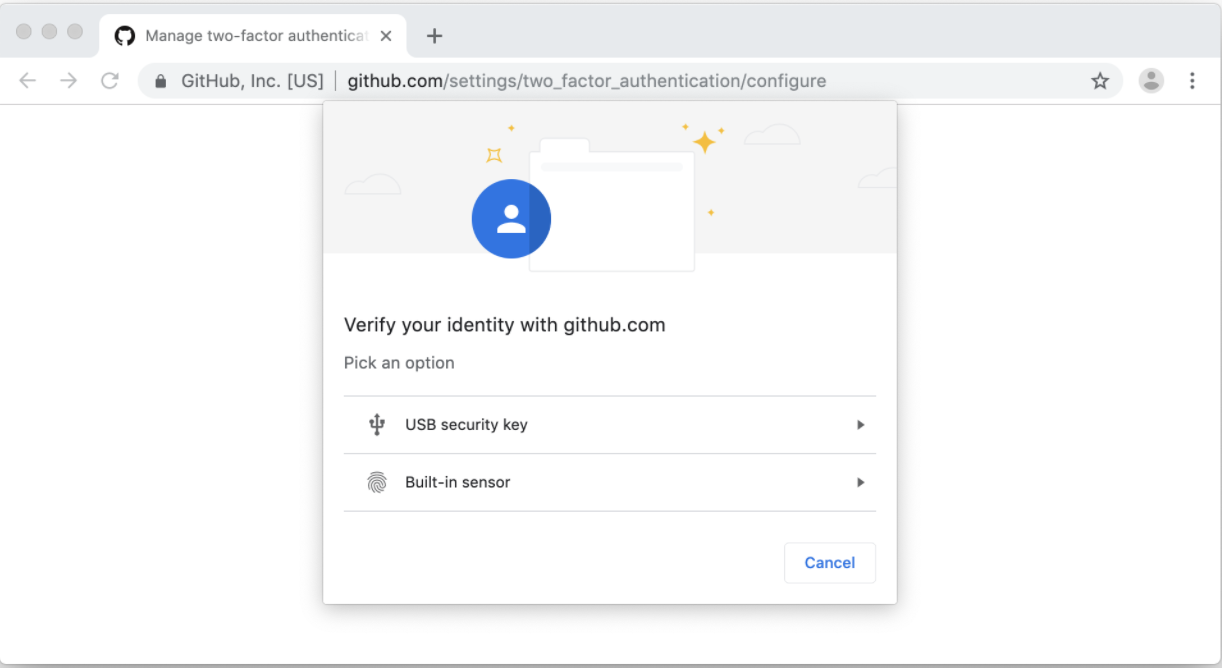
WebAuthn
WebAuthn uses public key cryptography to tie an “authenticator” to an individual.
Using a supported web browser you register your authenticator with your target service (Google, GitHub, etc.) which generates a public/private key pair. The public key is sent to the authentication server and completes the registration process. The next time you authenticate to your target service you must complete the two-factor challenge with your registered authenticator:
Image source: Github
Since many modern laptops have some hardware security module present it’s quite easy to use TouchID or Windows Hello as your authenticator, but you can also use USB-based security keys such as Yubikeys or Feitian keys. Google also allows you to register your phone as a physical security key leveraging their Smartlock application and your smartphone’s secure element.
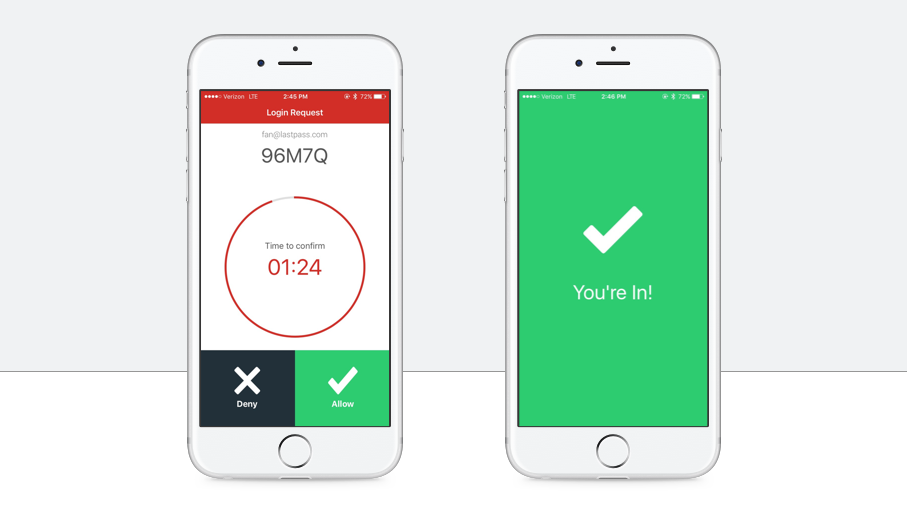
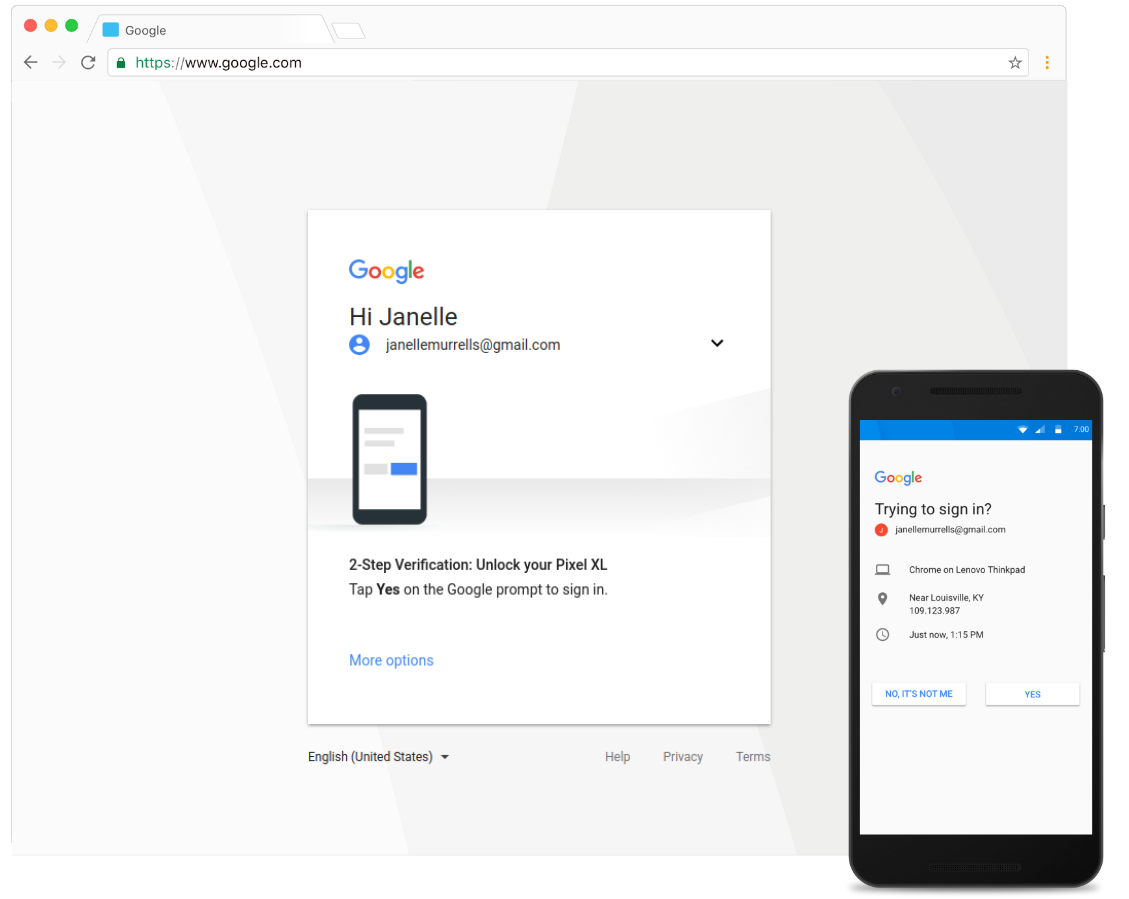
Push based 2FA
Popularized by Duo Security this method uses an on device push notification to verify a connection request. This is more convenient than typing in a six digit code and the notification typically gives you contextual login details such as IP address and browser to help verify the request. Google, OneLogin, Lastpass (and many others) provide this feature as part of their products.
Image sources: LastPass, Google
Make sure you generate backup codes!
When you enable two-factor authentication you are usually given the option of generating backup codes. If you don't have any way to access your authentication factor, backup codes can be used to complete your authentication challenge when you log into your target service. Usually each code can be used only once. It’s important to generate and store these codes someplace safe. A password manager vault would be the perfect place for these codes but you could also print them out and store them in your sock drawer (if someone is looking in there for backup codes, you’ve got bigger problems).
Which factor should you use?
Use the strongest authentication factor available to you. Ideally this would be using hardware backed 2FA but if this isn’t an option (or if you don’t feel comfortable using it) then look to TOTP or push based 2FA if available. 2FA Directory is a searchable directory of supported two-factor authentication options for popular service providers.
Image sources: 2FA Directory
Should I use SMS 2FA?
The NIST does recommend SMS as a delivery method for security codes. SMS 2FA has received a lot of coverage because of social engineering / SIM swapping attacks and the inherent flaws in the underlying SS7 communications protocol. To make matters more difficult SMS, may be the only method of delivery for the service you want to use. SMS should not be your primary 2FA delivery method but it should be enabled if it’s your only option as it will reduce risk against automated attacks.
🚨 2FA is not foolproof 🚨
Adding 2FA adds another layer to identity verification but it’s important to note that bad actors have found ways to subvert it. Even with 2FA it’s paramount to maintain good account hygiene. Create unique passwords per site or service. Enable account notifications for login attempts or new sign-ins if available. Limit third-party access to your accounts.
Summary
Bad actors will always use the simplest, most cost effective tactics to achieve their target goals. With the prevalence of data breaches and password reuse it’s become easy for bad actors to scale credential stuffing attacks. Enabling two-factor authentication is a low effort exercise that increases cost and effort to attackers and protects your account if your credentials are leaked. While there are a number of 2FA options I recommend the strongest form made available to you for each service.
Additional reading
A nice summary of how Twitter enabled their workforce to use hardware security modules and keys for strong two-factor authenication: https://blog.twitter.com/engineering/en_us/topics/insights/2021/how-we-rolled-out-security-keys-at-twitter
Twitter thread by Devdatta Akhawe on how his team pushed adoption of security keys and WebAuthn for use with Okta, and enterprise identity provider: https://mobile.twitter.com/frgx/status/1379504541666701313