Use a P**sword M*nager
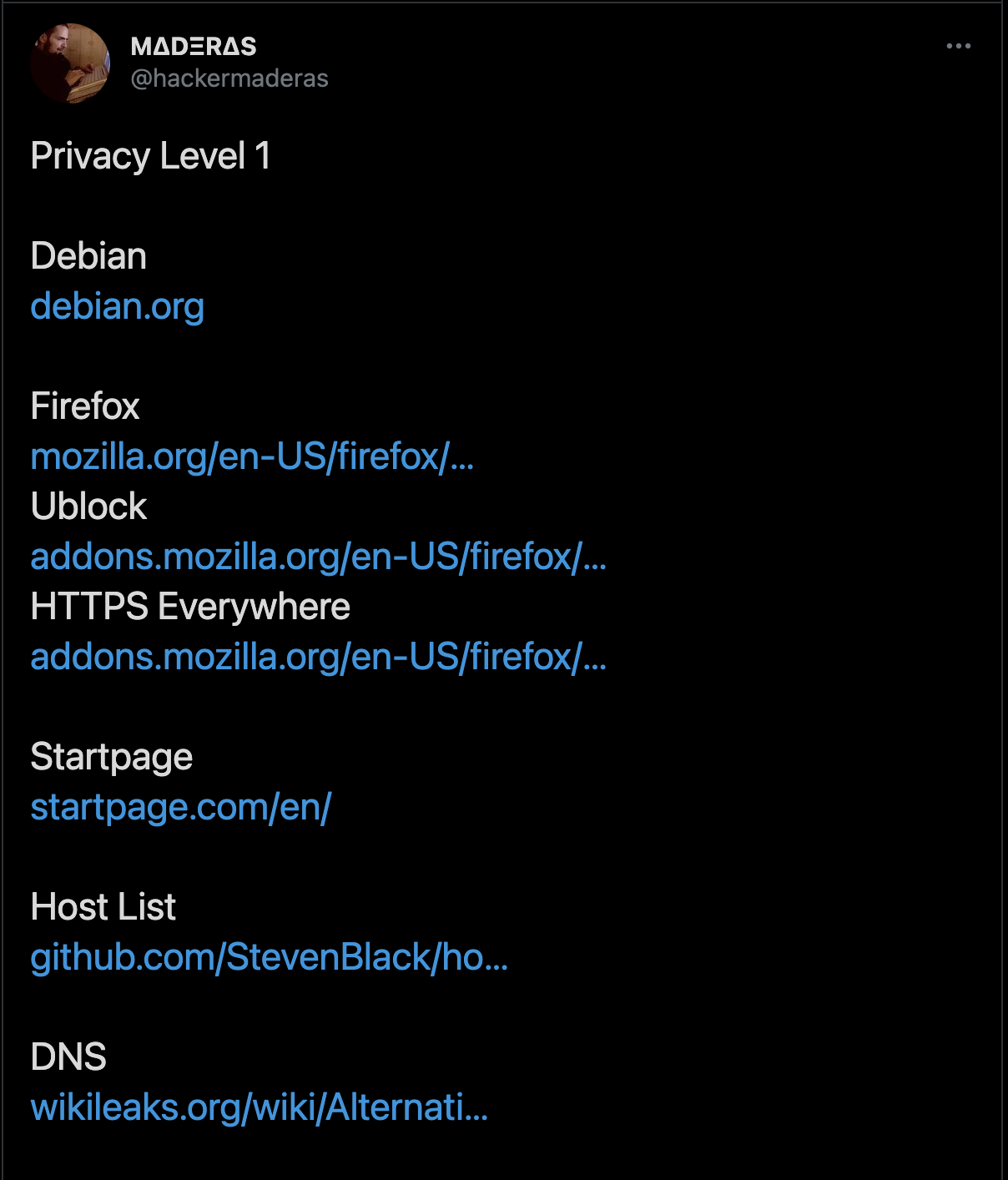
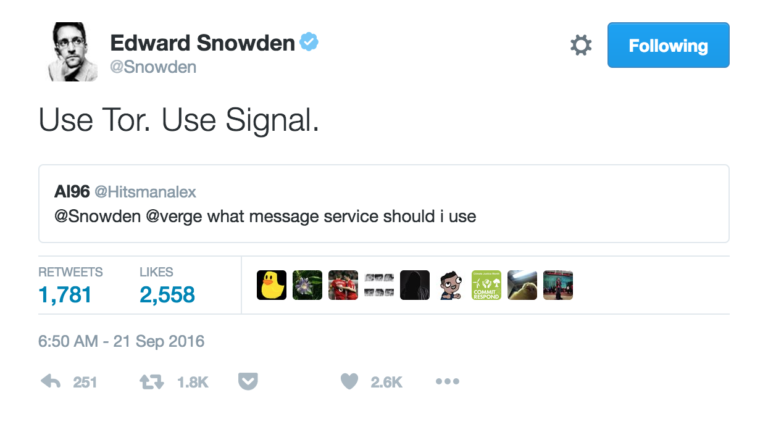
At the start of the New Year there’s the usual slew of resolutions that everyone makes. Promises to hit the gym more consistently. Be more thoughtful. Meditate more frequently. Clean the stove more often. Each of these resolutions can be attained by making small changes over time that eventually become habitual. The same can be said for online security habits. Stay close enough to Information Security (InfoSec) Twitter long enough and you’ll find lots of recommendations:
These recommendations are valuable to different people for different reasons but someone who is just starting to think about stepping up their online security practices may find these recommendations overwhelming. They also require more context. What do you gain by using Tor or Signal over a VPN and your phone manufacturer’s default messaging application? Under what circumstances should you use one or several of these recommended tools?
Audience
This is the first in a series of posts focusing on helping folks adopting security tools or practices. The goal here is to approach each as part of a checklist. We’ll explore the following:
Password manager ✅ 👈 this post
Two-factor authentication 🔜
HaveIbeenPwned 🔜
Browser security 🔜
Speed dating Intro to Threat Modeling 🔜
If you’re a seasoned security engineer or “tech savvy” the information will likely be familiar to you. However the descriptions or perspective in this blog post may be useful in explaining concepts or empowering others.
What is a password manager?
Password managers have become more prominent over the years. Many companies even purchase password manager licenses for employees to store credentials for internal applications. But what is a password manager and why should you use it? In short a password manager generates strong, unique passwords for you and stores them in a “vault”. You create a Master Password, which is responsible for securing access to your vault. This is the only password you need to remember and secure — the password manager will create and store all other passwords on your behalf. You can also also store other “secret” information within your vault, such as backup codes, bank pins, software licenses, or locker combinations.
How do bad actors typically gain access to accounts?
For the remainder of the post I will use the term “bad actor” to describe a hostile attacker or adversary. This term is not meant as a critique of acting skill 🥁
There are many ways a bad actor can gain access to username and passwords but these methods are the most prominent:
Bad password habits - If you’ve ever created a password before you typically lean heavily on things that are easy to remember and close to your heart such as pet names, birthdays, anniversaries. Unfortunately these details are usually sprinkled across public social media accounts and a bad actor can start to piece together potential passwords by looking at your social media accounts. Or worse, you may default to one of the many common passwords found on lists such as Nordpass’s Top 200 passwords of 2020 list.
Password reuse - Remember how long it took you to create a password the first time around? Well now you need to do it again! You also need to make sure you can remember it! But instead of creating a unique password for the next site you reuse one you’ve thought of previously.
Credential dumps - Company “X” was breached—generally the result of vulnerabilities on a system, which a bad actor then exploits—and username and passwords are inadvertently leaked. Credentials (username and passwords pairs) are then used to gain control of your account at “Company X” otherwise known as Account Take Over (ATO). Because password reuse is still prominent a bad actor can take your credentials from one dump and try to gain account access across multiple sites and services.
Why should you use a password manager?
Armed with knowledge of how bad actors can gain access to accounts, how can a password manager solve these problems for us?
The benefits of a password manager:
Create strong, unique passwords with little effort
Each password is randomly generated and both the length and criteria for generating the password can be changed easily depending on your needs. The password manager removes the burden of remembering or creating passwords across all the sites you log in to.Easy to “rotate” (change) a password if necessary
One of the pains of password management is changing or “rotating” a password. Let’s say you receive a notification from a site you use that suspects an unauthorized third party may have had access to some of your account details. Somewhere in that email it will likely say “Out of an abundance of caution you need to reset your password”.
Remember how long it took you to create a password the first time around? Well now you need to do it again! And if you’ve used that same password across other important accounts a bad actor may now have access to multiple accounts in your name. This begs the question — do you know how many sites you’ve reused this password with?
A password manager makes this process significantly less painful. If you need to change the password for any reason your password manager generates and stores the password for you, making it easy to change within minutes. Bonus: many commercial password managers have credential dump checks built into the product.Passwords are not sitting in a text file or spreadsheet in “plaintext”
I’ve known a few people who do try to create unique passwords per site but use spreadsheets or text documents to store their passwords. Their intentions are good but the passwords are stored in “plaintext.” That is, they are not encrypted and could be read by a person, computer application, or computer process that gains access to the file. Access control for spreadsheets (think Google Sheets) are flimsy. It’s quite easy to inadvertently leak your file to others, or worse, the public internet.
Access to your password vault is authenticated by your Master Password. The contents of your vault are encrypted on your local computer meaning a bad actor couldn’t simply read the contents of your vault by gaining access to a single file.Store other “secrets”
Credentials aren’t the only thing you likely want to protect from exposure — API keys, SSH private keys, a locker combination, even your bank pin are all candidates for storage in your in your vault.
How do password managers work?
All password manager systems typically consist of a local application installed on your computer that contains your vault and a browser extension. When you navigate to a site the browser extension uses a regex to determine if the site is stored in your vault. If so the browser extension will offer to autofill credentials associated with the stored site:
The browser extension also detects fields where a website expects you to input your username and password and offers to create a password if one does not exist in your vault.
Nice password yo.
Many commercial password managers sync to the cloud, making it easy to access your vault across multiple devices. This is convenient but there is a security tradeoff — you can access your passwords in more than one place but you are entrusting the password manager vendor to have proper detective and preventive measures in place to protect access to your sensitive data.
Understanding all the trade offs and threat modeling of this specific scenario isn’t part of this post but there are controls you can add that balance convenience and security, which is ultimately at the core of the decision making process to use any product or service.
What about my Master Password?
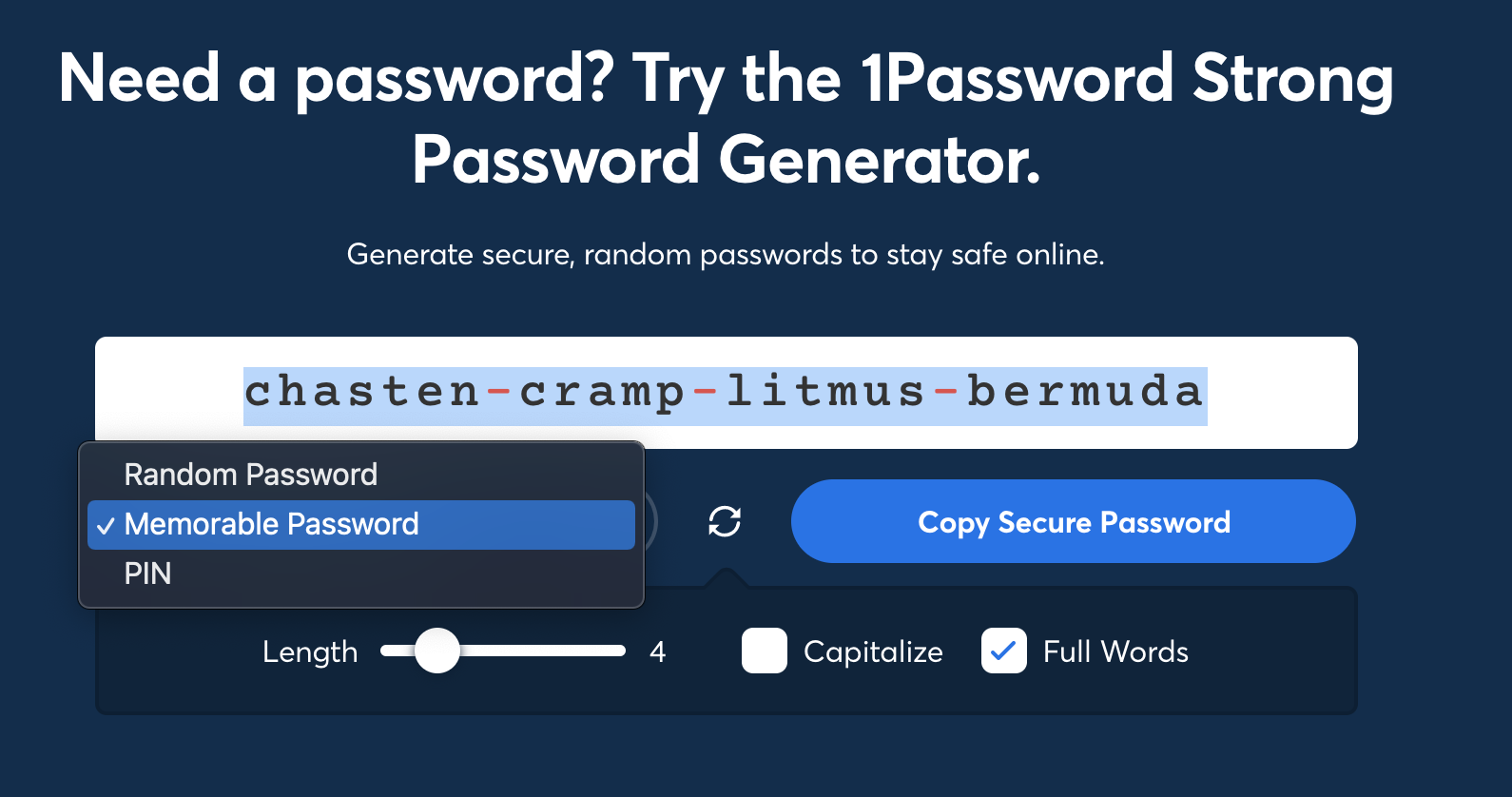
The only password you need to remember and secure is your Master Password. Since you’ll be using this password to log into your password manager frequently trying to remember a long, randomized character string isn’t going to cut it. Your brain may not be able to remember that randomized string but it can certainly be trained to remember a passphrase. A passphrase is a type of password that uses words with spaces or hyphens. An example:
repine-thames-obduracy-colander
The trick here is to use random, unrelated words. Don’t be afraid to make this passphrase silly or nonsensical. Four words should be sufficient, five+ is better. Write the passphrase down and keep it in your wallet. Once you’ve memorized it you can discard it. If you’re having trouble creating a passphrase 1 Password has an excellent online generator.
1 Password online generator
There is a learning curve….
I’ve used several password managers in both personal and professional contexts for over a decade. The first product I used was LastPass. It was challenging because I didn’t quite understand how the browser extension fit in with the flow of saving and changing passwords. I remember seeing the red dotted symbol in a website password field and thought “What the hell is that?”
The overall user experience—particularly with the local application—didn’t feel polished. I was also somewhat overwhelmed by the vast amount of security options I could tinker with instead of focusing on the core value of the product creating and securing passwords.
Unfortunately another hurdle is not all websites are clear about their password requirements when setting a password.
Why is this password invalid? ¯\_(ツ)_/¯
Screenshot courtesy of dumb password rules
Virtually all password managers allow you to create passwords of at least forty-characters with 1 Password and Lastpass supporting a max length of one-hundred characters! Since our password manager makes it easy to generate randomized passwords, cranking up the password length feels like a slam dunk choice but trying to shove a one-hundred character password into a password field that only supports a maximum length of twenty characters can add some friction to the process.
...but make it fun!
Don’t let that stop you! You can easily gamify the process of adding and rotating passwords you use. After you’ve added all old passwords to your vault create daily password change goals to train muscle memory and steadily make progress. All password managers tell you if your password is strong, weak, or worse:
Dang.
Set a goal of changing a “terrible” password within a certain time and reward yourself with a small piece of candy. If you really wanted to supercharge your efforts you could track the amount of time it took you to rotate your passwords, categorized by service type, ease of rotation based site password policy. The possibilities are endless.
The important thing here is to make it less of a chore and more habitual.
Which password manager should I choose?
It depends. You knew that was coming right?
Choosing a password manager requires some research. This excellent evaluation matrix is comprehensive but may be overwhelming to someone who wants to adopt a security tool or product for the first time. Your security requirements will differ between personal and business contexts. My advice would be think about these criteria:
Does the password manager support your desktop operating system, primary browser, and mobile device operating system?
Do you want the ability to sync across multiple devices for ease or do you want to maintain more control (and thus more responsibility to secure) the password database?
Look at the product. Does the user experience look and feel intuitive? Can you see yourself using it daily?
Do they have good documentation or white papers available to help you understand the product soup to nuts?
What support channels does the product have? Email, phone, Slack workspace?
Does support have dedicated service level agreements (SLA’s) for response?
Summary
Despite the learning curve to start using a password manager it adds significant value to your security toolkit. Once the workflow of generating and storing passwords feels natural your vault will quickly grow, and you’ll start thinking about what other sensitive information you might want to store in your vault. Remember to focus on making it a habit and not a chore.